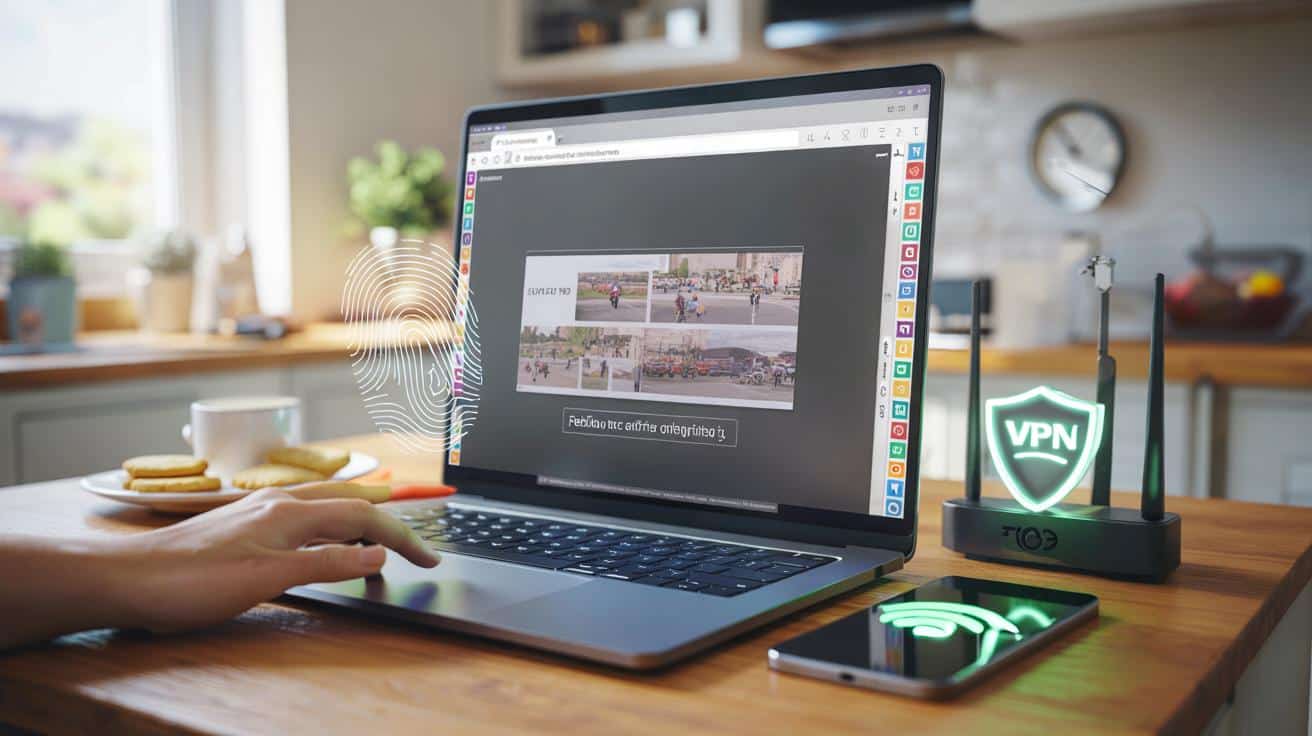
” A puzzle pops up. A checkbox blinks. Your flow shatters. It’s not just you, and it’s not just today. The web is testing you because your browsing looks a little too fast, a little too private, a little too unpredictable.
The kettle clicks off, the house is quiet, and you’ve got five minutes before the school run. Two tabs for news, one for tickets, one for banking, and—why not—holiday deals. You tap a link and a grey box slides in: “Are you a robot?” You click, it reloads, it asks again. The page feels colder each time. Your coffee cools while you pick bicycles from a grid of wonky pictures. Yes, it feels personal. A neighbour WhatsApps a meme; your screen asks for traffic lights. Something thinks you’re a robot.
Six behaviours that trigger the “verify you are human” screen
Web defences don’t read your mind. They score your behaviour. Bursts of speed are a giveaway: ten clicks in a few seconds can look scripted. Opening a dozen tabs of the same site makes you resemble a scraper. A fresh incognito window, no cookies, and a privacy extension blocking scripts can feel like a mask. Add a VPN hop or mobile tether and your IP looks “new” to every page. **That’s not evil—it’s just risky in the eyes of a bot filter.**
Picture a Wednesday lunchtime. You’re on café Wi‑Fi, your phone is tethered, and your browser time is a minute out. You refresh the ticket page, again and again, because the seats keep vanishing. The site sees rapid requests from a shared hotspot, a device that won’t run one small script, and an IP that changed countries five minutes ago. To a human, that’s normal hustle. To an anti‑bot system, it’s a neon sign.
Under the bonnet, risk engines blend signals: IP reputation, request velocity, and “browser fingerprint” details like fonts, headers, even battery queries. **Six frequent triggers** keep popping up in user logs: 1) VPN or proxy exit nodes, 2) high‑speed clicking or refresh bursts, 3) lots of parallel tabs or price pages, 4) aggressive blockers that break page scripts, 5) clock or timezone mismatches, and 6) odd fingerprints from rare extensions or modified user‑agents. The result isn’t just friction. Three risks ride along: session loss and failed checkouts, over‑sharing data with third‑party CAPTCHA services, and fake “verification” pages used by phishers. The web is judging, fast.
How to stop them now (without breaking your browsing)
Start with a 60‑second reset. Pick one browser you trust, update it, and log in to the site if you have an account. Enable JavaScript and first‑party cookies for that domain only. Turn off your VPN for a minute or lock it to a stable UK exit. Then reload calmly—no blitz of clicks—so the risk score can settle.
The next fix is tidy, not drastic. Keep privacy tools, just let core scripts run on pages you use often. Whitelist your bank, your travel site, your favourite shop. Stick to one connection—home Wi‑Fi over tether—when doing sensitive tasks. Check your device clock; even a small skew looks robotic. Let’s be honest: nobody does that every day. Try it once this week and watch those tests fade.
There’s a mental shift too: behave less like a bot and you’ll be treated less like one.
“The easiest way to look human online is to act like a steady, single person: one browser, one IP, predictable clicks,” says a security engineer who builds these filters.
- Enable JS and first‑party cookies for the site you need.
- Use one browser profile and keep it updated.
- Pause VPN/proxy or stick to a consistent local exit.
- Close duplicate tabs; slow refreshes to every 10–15 seconds.
- Fix system time and timezone; match your region.
- Disable “link checker” or “privacy hardening” extensions on trusted sites.
What this friction is really telling you
These pages aren’t accusing you. They’re nudging you back toward a pattern the web understands. If you treat every site like an adversary—no cookies, no scripts, mystery IP—you’ll be treated like one. If you travel with a light footprint—consistent identity, stable connection, simple clicks—the gates open. It’s a quiet bargain.
The trick is balance: guard your privacy where it matters, and relax the shield where you need speed or trust. Share this with someone who grumbles at “pick the pedestrian crossings” squares. The small fixes often come for free, right there in the way you click. Your habits tell a story before your words do. **Change the story and the checkpoints melt away.**
| Point clé | Détail | Intérêt pour le lecteur |
|---|---|---|
| Six behaviours | VPN/proxy use, rapid clicks, many parallel tabs, script/cookie blocking, clock skew, unusual fingerprints | Spot what you’re doing that triggers checks |
| Three risks | Lost sessions and carts, data shared with CAPTCHA vendors, exposure to fake “verification” pages | Avoid wasted time and security pitfalls |
| Stop them now | One‑minute reset, stable connection, site whitelisting, slower refreshes, extension hygiene | Immediate, realistic fixes without losing privacy |
FAQ :
- Why do I see “verify you are human” on my home Wi‑Fi?Your IP may have a poor reputation from previous users, or your browsing looks bursty. A router reboot can rotate the IP. Using one updated browser with JS/cookies on for that site usually helps.
- Does a VPN always trigger these pages?Not always, but many VPN exits are shared and noisy. Stick to a nearby exit and keep it consistent. For logins or checkout, try pausing the VPN briefly.
- Can I avoid CAPTCHAs without sacrificing privacy?Yes—whitelist only the sites you trust. Keep privacy tools on elsewhere. Allow first‑party cookies and required scripts on those trusted domains, not across the board.
- Are these verification pages safe?Legitimate ones come from known providers and keep you on the same domain. Watch for odd URLs, full‑screen pop‑unders, or downloads. If in doubt, close the tab and navigate fresh.
- Why does it happen more on my phone?Mobile IPs can hop as you move networks. Battery savers and content blockers also break scripts. Use Wi‑Fi at home, keep one mobile browser updated, and allow the site’s core scripts.